How to Protect Software Source Codes with an NDA

If you have ever thought about creating software or even licensing it, you’ll probably have come across something called software source codes.
Source codes are generally divided into two types:
- Proprietary
- Open source
For example, when you install Apple’s software, the source code is proprietary. Apple does this on purpose to protect its intellectual property and to prevent a user from making changes to the source code without Apple’s permission.
Open source codes such as those under the GNU General Public License is free for anyone to modify, use and share with others. The purpose for open source codes is to encourage programmers to collaborate to improve the codes and help make it more useful and powerful for everyone.

After 1974, the US Commission on New Technological Uses of Copyrighted Works (CONTU) declared that computer programs including software source codes could be copyrighted.
Proprietary source codes can be protected through intellectual property rights including copyright laws, trade secret laws and patents.
In addition to these intellectual property rights, you can also use a non-disclosure agreement to protect your proprietary source codes.
Enter the NDA
A non-disclosure agreement (NDA) is basically a contract between parties wherein the party that receives confidential information (the Recipient Party) agrees to be bound by secrecy and not to expose or misuse the confidential information without the permission of the party that’s sharing the confidential information (the Disclosing Party).
An NDA can be unilateral (or one-way) where only party makes disclosures of confidential information and the other party agrees to be bound to confidentiality and not misuse the information.
In a mutual agreement, both parties disclose confidential information that they wish the other party to keep secret.
Normally in a mutual agreement, the bargaining power is much more equal and the terms of the agreement are created for the benefit of both parties, not just the party that’s making the disclosures.
NDAs are extremely useful in business relationships as it allows parties to have initial discussions without fear of their trade secrets or other types of confidential information being exposed or stolen.
How to protect source code with NDA
1. Source code is confidential information

An effective NDA should always provide a definition of what would be considered confidential information.
This is to make it clear to the party who’s going to have access to the source code what information needs extra care and privacy.
Besides software source codes, you can include other valuable information in your definition of confidential information such as:
- Designs
- Marketing material
- Customer lists
- And so on
However, there’ll probably be information that you share during the course of the project that will not qualify as confidential information.
This includes information that’s already widely known to the public, information that the Recipient Party may already had access to prior to you giving information about your project.
For these kinds of information, there’s no need for an obligation of confidentiality. To demand confidentiality for these types of information may actually invalidate or dilute the effectiveness of your NDA.
Here’s an example of a clause that defines what is confidential information and what is not from Wingware Python IDE’s NDA:

You could also protect your software source code by using an overall definition that covers everything related to the finished product (application).
Here’s an example from AllMerchants website:
![]()

Your software, including parts of its source code, can also made up of algorithms.
For example, if you’re worried that the freelancer might misuse your software source code in a different programming language, you could define the algorithm or description of the functionality of the source code as the confidential information rather than the source code itself.
Similarly, if you work in diagrams, data flows and other types of results produced by the source code, you can choose to protect these in your definition of confidential information rather than protecting the source code itself.
2. Stop disclosures of source code

It’s fairly obvious but you should always include a clause that expressly provides that the other party is prohibited from disclosing your confidential information (which can include the finished software, its source code, algorithms etc.) to third parties without your permission.
Here’s an example of a clause from Wingware Python IDE’s NDA:

3. Source code should not be used

If you disclose information about your software application, but not necessarily the source code itself, you may wish to specifically state that the other party is not allowed to use the software’s source code (if the code can be seen or accessed) her/his other work, without your permission.
Here is another example from Wingware Python IDE’s NDA:
![]()
4. Source code should not be stored or copied

Unlike physical documents that are physical, software and its source code can be easily copied, hidden away on electronic devices without easily being detectable or stored in a manner that if forgotten, is really theft.
You could use your NDA to expressly state how the source code can be, or cannot be, stored by the other party.
Consider this example from AllMerchants website:

5. Do not transfer rights

If you intend to share anything that’s proprietary with the other party, you can include a clause that specifically states that no rights, including licensing rights, shall be transferred to the other party as a result of your sharing of confidential information.

On the other hand, if you disclose the source to a freelancer/independent contractor that will work on your software project, you want to make sure that any work produced by the freelancer during the project becomes yours, especially if you have paid for the work.
Unless you state specifically otherwise, the freelancer is the automatic owner of the work she/he produced. Here’s an example of a clause that clearly states that all work produced would be considered “work for hire” which means that all proprietary rights in the work will be assigned automatically to you or your company.
Here’s an example from Apriorit’s Software/R & D Outsourcing:

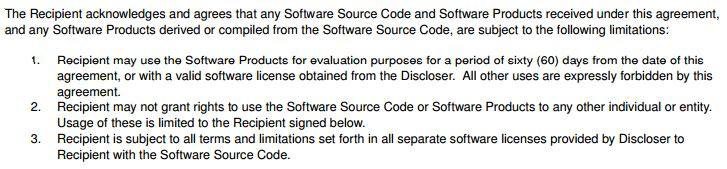
6. Source code is only for test and evaluation

It’s not uncommon for companies to hire freelancers to test their software, discover bugs, and provide feedback to help the company improve on the software application.
If you intend to hire a party (a freelancer/independent contractor or another company) to test your software, you should also make effort to protect your confidential information by expressly providing that the software source code or its end product is only to be used for evaluation purposes and no other uses are permitted.
It should also be clear that no rights are granted for access to the software as well.
Here’s an example of a clause from Wingware Python IDE’s NDA:
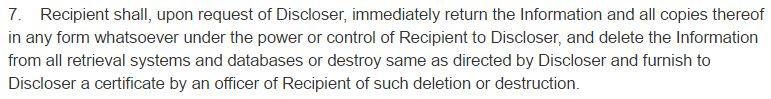
7. Return the source code

To reduce the likelihood of misuse, theft or exposure of your software’s source code, you can use an NDA to expressly provide that you want all confidential information – and copies of such information – to be returned to you or deleted.
If your software and all its related information and documents will be seen and accessed by multiple parties (employers, consultants, freelancers working with the other party), you could also insert a clause requesting for a list of all parties that had access to your confidential information.
Using this list, you can perform an individual check with each party to ensure that all information has been returned to you or deleted. This list is also useful for any breaches that may occur in the future as it helps you to track down with whom or where the breach might have occurred.
8. Governing Law

To prevent any misunderstandings or conflict of laws, you should insert a clause that specifies which governing law is to apply in case of any disagreement with regards to the terms of the NDA.
You can also expressly provide which jurisdiction is to apply to the agreement.
“Jurisdiction” refers to the courts that will be entitled to rule on any dispute.
Although this can present a different set of challenges, you can choose to have governing laws and jurisdictions from different areas.
For example, you could choose to have British law apply in an American jurisdiction.
This means that you want an American court to apply British laws when upholding the NDA.
Here’s an example of a clause taken from the European IPR Helpdesk’s Mutual Non-Disclosure Agreement:

When it comes to retail software, most companies use an end-user license agreement (EULA) to protect their software.
Such agreements normally prohibit reverse engineering, analysis or modification of the software.
However, when you’re hiring a freelancer to do things with your software source code that an end-user (the customer who’s going to use the finished software product) is prohibited from doing, then you need a different set of tools to protect yourself.
Although no legal instrument is perfect, an NDA can be very useful for this purpose.
Credits. The following icons are from The Noun Project: “Unlock” by Ralf Schmitzer, “transfer” paper by sevgenjory, “Bug report” by Lemon Liu, “Code Stub” by Richard Slater, “Flow Chart” by Chameleon Design.
Nov 28, 2017 | Non-disclosure Agreements
This article is not a substitute for professional legal advice. This article does not create an attorney-client relationship, nor is it a solicitation to offer legal advice.